It is recommended that you install and configure the Certificate Enrollment Policy Web Service using the
InstallConfigCEP.ps1 PowerShell script provided by Entrust. This script requires the TLS certificate previously obtained in Issuing TLS certificates for the Certificate Enrollment Policy Web Service.
To install and configure the Certificate Enrollment Policy Web Service using a PowerShell script
- Install a supported version of Microsoft Windows Server (if not already installed), and join it to the Windows domain.
- From Entrust TrustedCare, download the PowerShell scripts for Certificate Enrollment Gateway.
- Extract the PowerShell scripts to a directory on the server.
- PowerShell scripts downloaded from the Internet may be blocked from running. To unblock a PowerShell script:
- Right-click the PowerShell script > Properties.
A Properties dialog box appears. - Under the General tab, click Unblock.
- Right-click the PowerShell script > Properties.
- Open an elevated PowerShell window. Select Start > Windows PowerShell, then right-click Windows PowerShell > Run as administrator.
- Navigate to the directory where you extracted the PowerShell scripts.
Enter the following command to run the
InstallConfigCEP.ps1script:.\InstallConfigCEP.ps1The script validates the pre-requisites, and then installs any required Windows packages or features. For example:
The PowerShell script was tested on specific versions of PowerShell. When validating the prerequisites, the PowerShell version my be listed as Unverified, an "Unverified" version of PowerShell indicates that the script was not tested on that version of PowerShell. You can still use the script on an "Unverified" version of PowerShell.
Validating pre-requisites:Script-Mode: WindowsScript Version:1.5.1.19- Member of Domain: Verified- Domain Admins privileges: Verified- Enterprise Admins privileges: Verified- Windows Version: Verified (Microsoft Windows NT10.0.17763.0)- PowerShell Version: Verified (5.1.17763.2931)------------------------------------------------------------Installing ADCS-Enroll-Web-PolADCS-Enroll-Web-Pol installedCheckingforWeb-Mgmt-ConsoleInstalling Web-Mgmt-ConsoleCheckingforWeb-Mgmt-CompatInstalling Web-Mgmt-CompatThe script prompts you to select the authentication type:
CEP Authentication SettingChoices :Name Value---- -----UserName4Kerberos2Select Authentication Type [Default:2]:To select user name and password authentication, enter 4.
User name and password authentication is the only authentication mode supported by non-domain enrollment endpoints.- To select Kerberos (Windows integrated) authentication, enter 2.
The Certificate Enrollment Policy Web Service requires a certificate. The script prompts you to select a certificate option:
A CEP webserver certificate has not been selected.Choose from the following Options:[S] Select Existing Cert [N] Supply New Certificate [C] Continue with selected Certificate [E] Exit [?] Help(defaultis"S"):To select an existing certificate, enter
S.- To supply a new certificate, enter
N.
If you chose to select an existing certificate:
The script will search the server for existing TLS Web certificates.
The script will first search for a certificate assigned to the Default Web Site in Microsoft IIS. If no certificate is assigned to the Default Web Site, the script will then search the certificate store of the local computer for valid (not expired) certificates with the following:- a subject name with the fully qualified domain name (FQDN) of the host
- a private key
- an extended key usage of Server Authentication
If the script finds a valid certificate, it asks if you want to use the certificate. For example:
SearchingforExisting Certificate(s)A certificate was found.Subject : CN=cepusername.example.comIssuer : CN=cepusername.example.comKeyUsage : DataEncipherment, KeyEnciphermentEKU List : Server Authentication (1.3.6.1.5.5.7.3.1)DNS SAN : cepusername.example.comSerial Number : 37F2440E97A3AE8046AA54BD7227FAFCThumbprint : 50C09642942060AE1A58C5C3006F2455B57326BCNot After :09/05/202320:00:00PolicyId :Continue with above Certificate? (y/n):- To continue with the certificate found by the script, enter
y. - To go back and provide a different certificate, enter
n.
- To continue with the certificate found by the script, enter
If the script finds multiple valid certificates, it will prompt you to select a certificate. For example:
SearchingforExisting Certificate(s)More than one certificate with FQDN cepusername.example.com has been found.Certificate Index :1-----------------Subject : CN=cepusername.example.comIssuer : CN=cepusername.example.comKeyUsage : DataEncipherment, KeyEnciphermentEKU List : Server Authentication (1.3.6.1.5.5.7.3.1)DNS SAN : cepusername.example.comSerial Number : 1862326CAB4507B1411EA7624F6DDDBAThumbprint : EEC5FF53EA64B1B56B8731A7E73C058257A4DC0ENot After :09/06/202320:00:00PolicyId :Certificate Index :2-----------------Subject : CN=cepusername.example.comIssuer : CN=cepusername.example.comKeyUsage : DataEncipherment, KeyEnciphermentEKU List : Server Authentication (1.3.6.1.5.5.7.3.1)DNS SAN : cepusername.example.comSerial Number : 37F2440E97A3AE8046AA54BD7227FAFCThumbprint : 50C09642942060AE1A58C5C3006F2455B57326BCNot After :09/05/202320:00:00PolicyId :Please select the Index to select a Certificate.0toreturnto previous menu.:- To select one of the existing certificates, enter the index number associated with the certificate.
- To go back and provide a different certificate, enter 0.
- To select one of the existing certificates, enter the index number associated with the certificate.
- If you chose to supply a certificate:
The script prompts you to provide the certificate:
Please enter full path to certificate file including the filename :Enter the full path and file name of the certificate, in PFX or P12 format.
- When prompted, enter the password of the certificate file.
If the supplied certificate has a subject that does not match the fully qualified domain name (FQDN) of the host, the script displays a warning and asks if you want to continue with the certificate. For example:
The supplied certificate has a subject that does not match the FQDN ofthishost.Host FQDN : cepusername.example.comSupplied certificate details:-----------------------------Subject : CN=CEP Web Service, CN=CA Entry, O=Example, C=USIssuer : CN=CA Entry, O=Example, C=USKeyUsage : KeyEncipherment, DigitalSignatureEKU List : Server Authentication (1.3.6.1.5.5.7.3.1) Client Authentication (1.3.6.1.5.5.7.3.2)DNS SAN : cepusername.example.comSerial Number : 6AFEE3C47A569F95A9C5622D679B42C1Thumbprint : 2E6601A98E2ADBD4EBE5DF6D8C3A514CD7660BADNot After :09/06/202513:55:27PolicyId :Continue with above Certificate? (y/n):- To continue with the certificate, enter
y. - To go back and provide a different certificate, enter
n.
- To continue with the certificate, enter
After providing a certificate, the script displays information about the certificate, and prompts you to select a certificate option:
Selected Webserver CertificateforCEP:Subject : CN=cepusername.example.comIssuer : CN=cepusername.example.comKeyUsage : DataEncipherment, KeyEnciphermentEKU List : Server Authentication (1.3.6.1.5.5.7.3.1)DNS SAN : cepusername.example.comSerial Number : 1862326CAB4507B1411EA7624F6DDDBAThumbprint : EEC5FF53EA64B1B56B8731A7E73C058257A4DC0ENot After :09/06/202320:00:00PolicyId :Choose from the following Options:[S] Select Existing Cert [N] Supply New Certificate [C] Continue with selected Certificate [E] Exit [?] Help(defaultis"S"):- To go back and select a different existing certificate, enter
S. - To go back and supply and different certificate, enter
N. - To continue with the selected certificate, enter
C.
- To go back and select a different existing certificate, enter
After providing a certificate, the script prompts you to provide a Windows user to configure the Certificate Enrollment Policy. The user must have Domain Admin and Enterprise Admin permissions.
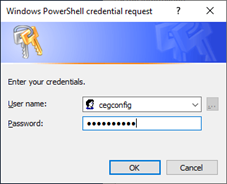
Configuring CEP ServicePlease enter the user information to be able to configure CEPThe user must have Domain Admin and Enterprise Admin rightscmdlet Get-Credential at command pipeline position 1Supply values for the following parameters:Credential
Enter the user name and password credentials of the Windows user.The script installs the Certificate Enrollment Policy Web Service, then prompts you to provide a friendly name for the service:
Installing AdcsEnrollmentPolicyWebServiceAuthentication : UserNameSSLThumbprint : DE45D685512D0F58A4CA7A60A485D8FD03723276Install CompletePlease enter the 'Friendly Name' for the CEP Service :Enter a friendly name for the Certificate Enrollment Policy Web Service. The friendly name must be unique for the domain. The friendly name will appear in some interfaces. For example:
WSTEP UserName CEP.To properly function with an existing Microsoft CA, the Certificate Enrollment Policy Web Service requires a UUID (Universally Unique Identifier). The script asks whether you want to generate a UUID or supply an external UUID.
All instances of the CEP Service must use the same UUID.You must generate the UUID for the first instance, then supply the UUID for all subsequent instances.Generate or supply a UUID for the CEP Service?Generate a UUID 1Supply a UUID 2Enter Selection ( 1 | 2 ) :If you are installing the initial instance of the Certificate Enrollment Policy Web Service and you want the script to generate the UUID, enter 1. For example:
Generating Unique UUIDUUID 6e42b254-0302-4428-9bc5-c34d11c3b4b6WARNING: Use the same UUID on all the CEP instances for Entrust WSETP.Selected UUID : 6e42b254-0302-4428-9bc5-c34d11c3b4b6Record the generated UUID. All instances of the Certificate Enrollment Policy Web Service must use the same UUID for Entrust WSTEP enrollment.
If you are installing subsequent instances of the Certificate Enrollment Policy Web Service and you want to supply the UUID generated in the first instance, enter 2. For example:
Enter a unique valid UUID : 1435d47b-a043-4b39-9420-0ff067344e4eSelected UUID : 1435d47b-a043-4b39-9420-0ff067344e4eWhen using Kerberos authentication, you can obtain the UUID of the installed Certificate Enrollment Policy Web Service by entering the following PowerShell command:
(Get-WebConfigurationProperty -pspath "MACHINE/WEBROOT/APPHOST/Default Web Site/ADPolicyProvider_CEP_Kerberos" -filter "appSettings/add[@key='ID']" -name "value").valueWhen using user name and password authentication, you can obtain the UUID of the installed Certificate Enrollment Policy Web Service by entering the following PowerShell command.
(Get-WebConfigurationProperty -pspath "MACHINE/WEBROOT/APPHOST/Default Web Site/ADPolicyProvider_CEP_UsernamePassword" -filter "appSettings/add[@key='ID']" -name "value").value
The script asks if you want to continue with the provided UUID:
Continue with above UUID? (y/n):- To continue with the provided UUID, enter
y. - To go back and change the UUID, enter
n.
- To continue with the provided UUID, enter
The script asks if you want to restart Microsoft IIS:
Recommended: Restart IISRestart IIS now ? (y/n):It is recommend that you restart Microsoft IIS to ensure the changes are applied.
- To have the script restart Microsoft IIS, enter
y. - To not restart Microsoft IIS, enter
n.
It is recommended that you manually restart Microsoft IIS to ensure that the changes are applied.
- To have the script restart Microsoft IIS, enter