When you create a credential for External Account Binding, an HMAC (Hash-Based Message Authentication Code) key is created for that credential. Each External Account Binding credential has its own HMAC key. Each ACMEv2 client that enrolls with an External Account Binding credential will use the HMAC key only once. An ACMEv2 client will use the HMAC key only when it initially connects to the ACMEv2 server and creates an ACMEv2 account. After the account is created, the ACMEv2 client no longer needs the key.
When an HMAC key is disabled for an External Account Binding credential, new ACMEv2 clients are blocked from using the key to create new accounts. ACMEv2 clients that have already used the key to create an account can still perform ACMEv2 operations if the ACMEv2 operations are enabled for the External Account Binding credential.
You can enable a key that has been disabled for an External Account Binding credential. When you enable a key, new ACMEv2 clients can use the key to create a new ACMEv2 account.
To enable the HMAC key for an External Account Binding credential
- On the Entrust Deployment Manager or Cryptographic Security Platform node hosting the EAB Utility, log in as sysadmin.
- Enter the following command to launch the EAB Utility:
sudo eab-util - The main menu appears:
- Select Manage EAB credentials, and then press Enter.
A list of External Account Binding credentials appears. For example:
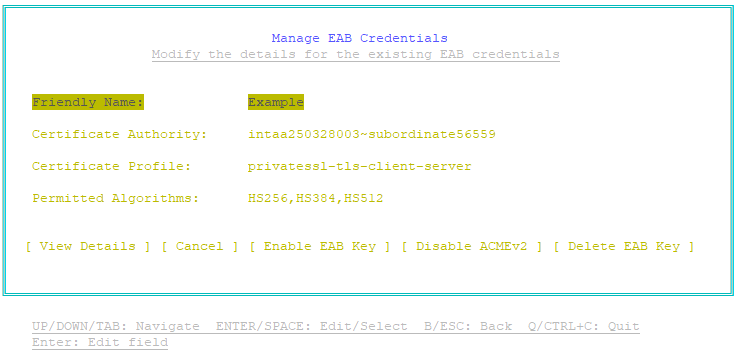
The Key Status column displays the status of the HMAC key for each External Account Binding credential, either Enabled or Disabled. - Select the credential whose HMAC key you want to enable, and then press Enter.
A Manage EAB Credentials page appears. For example: - Select Enable EAB Key, and then press Enter.
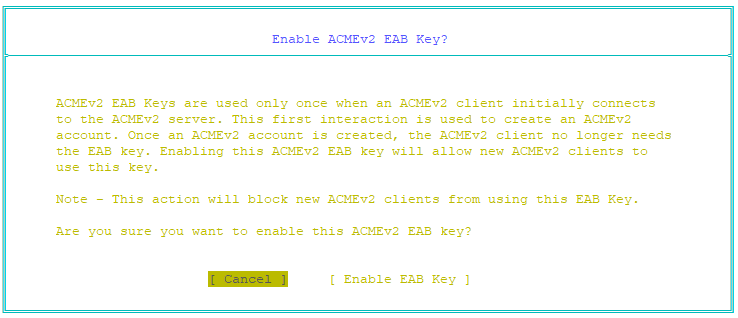
The Enable ACMEv2 EAB Key page appears. - Select Enable EAB Key and press Enter.
The HMAC key for the External Account Binding credential is enabled. The Manage EAB Credentials page reappears