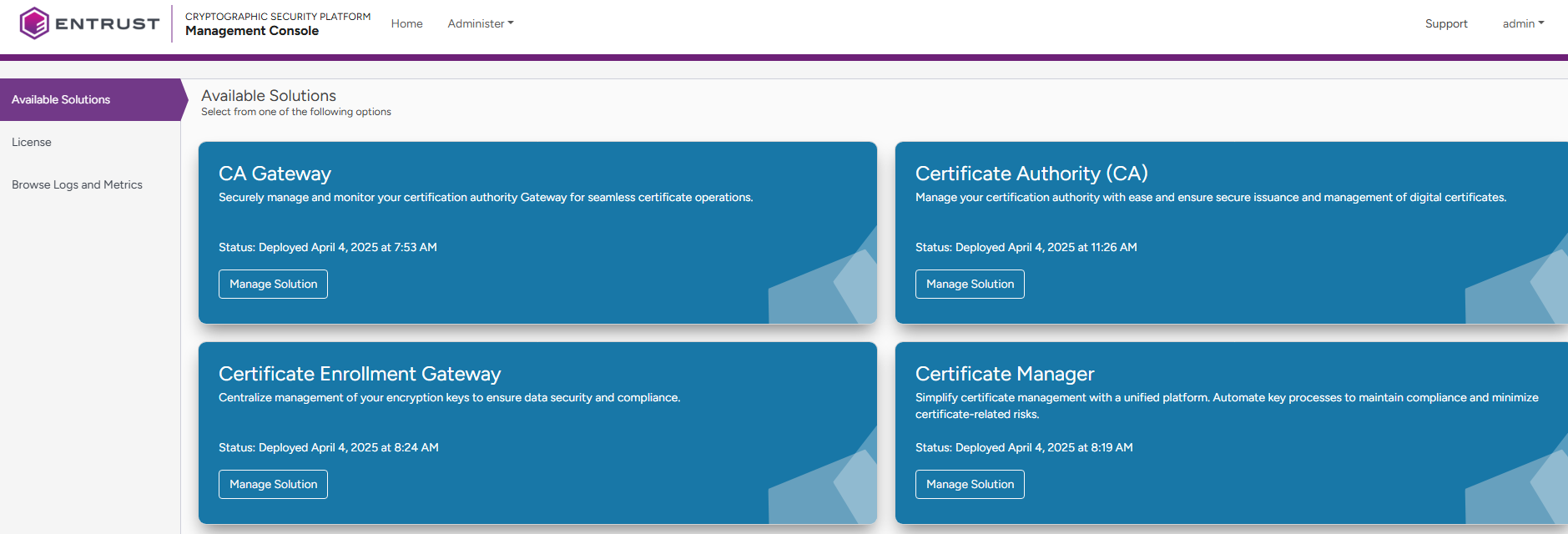
See below for configuring and deploying Certificate Manager with the Management Console.
Do not forget to also click Deploy after each update of the configuration or the license file.
To configure and deploy Certificate Manager with the Management Console
Open the following URL in a Web browser.
https://<machine>/management-consoleWhere
<machine>is the IP address or domain name of the machine hosting Cryptographic Security Platform.- Log in to the Management Console as a user belonging to a role with Certificate Manager management permissions – for example, the initial
adminadministrator user.See Starting up the Management Console for how to manage users and roles.
- In the content pane, click Manage Solution under Certificate Manager.
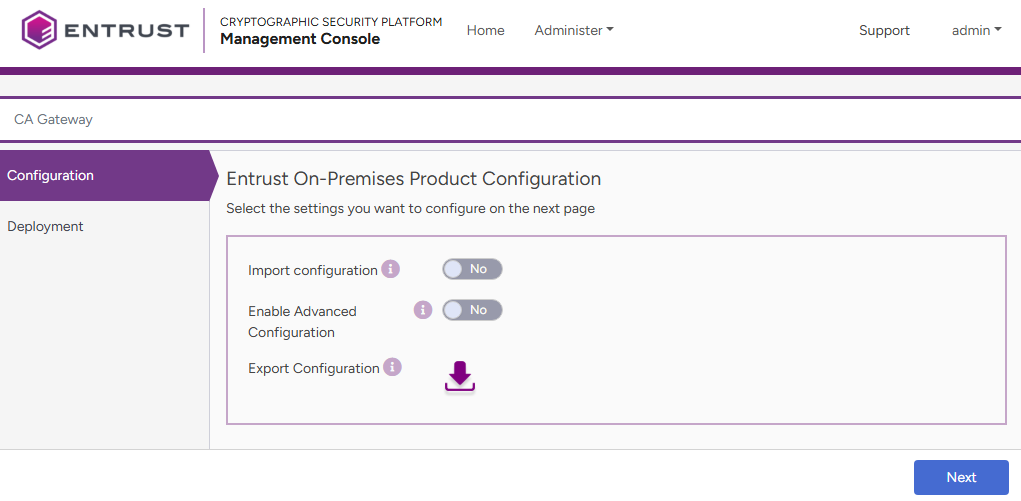
Toggle Import Configuration if you want to import a configuration file previously generated with the Export Configuration option.
- Toggle Enable Advanced Configuration if you want to configure the full set of configuration parameters supported by the solution.
- Click Next.
- Configure the solution settings described in the following sections.
- CM Hostname
- Discovery Scanner version
- Initial Administrator Username
- Initial Administrator Password
- Initial Administrator Email
- Name of the PostgreSQL Database
- Database User Name
- Database User Password
- Host of the PostgreSQL database
- External database port
- SSLMode for the PostgreSQL external database
- CA Certificate(s)
- Click Validate to validate the configured settings.
- Correct any detected configuration error until the Validate option displays no warnings.
- Optionally, click the Download button to export the current configuration. You can later import this configuration using the already mentioned Import configuration toggle switch.
- Click Submit and wait while Cryptographic Security Platform uploads the configuration and any attached file, such as a P12 file with authentication credentials.
- Click Deploy.
CM Hostname
The base hostname of the Kubernetes Ingress routing to the application.
Mandatory: Yes.
Discovery Scanner version
The version of the Entrust Discover Scanner integrated with Certificate Manager.
Mandatory: No. Skip this field when Certificate Manager is not integrated with Discover Scanner.
Initial Administrator Username
The username of the initial administrator.
Mandatory: Yes.
Initial Administrator Password
A temporary password for the initial administrator. Ensure that this temporary password does not include special characters such as '#', '!', or '*'.
After the initial login, the administrator will be prompted to create a new password that meets a specific set of password strength requirements
Mandatory: Yes.
Initial Administrator Email
The email address of the initial administrator.
Mandatory: Yes.
Name of the PostgreSQL Database
The name of an external PostgreSQL database meeting the Database requirements. The Certificate Management deployment process will automatically create all the required tables.
Solution databases can be hosted on the same DBMS. However, do not merge tables from different solutions into a single database, as each solution requires a dedicated database.
Mandatory: Yes.
Database User Name
The user name of the external PostgreSQL database.
Mandatory: Yes.
Database User Password
The user password of the external PostgreSQL database.
Do not include special characters such as "#", "!", or "*" in the user password.
In case this password changes in the external database.
- Update the value also on this field of the Management Console.
- Click Submit and wait while the new configuration is applied.
- Click Deploy.
- Open a command line session on any installation node.
- Run the following command.
sudo kubectl get deploy -o name -n certhub | xargs -n1 sudo kubectl rollout restart -n certhub
Mandatory: Yes.
Host of the PostgreSQL database
The IP address or Fully Qualified Domain Name (FQDN) of the database host.
As explained in Database requirements, the SSL certificate for the database host must include the IP address or FQDN of the host.
Mandatory: Yes.
External database port
The connection port with the external PostgreSQL database.
Mandatory: Yes.
SSLMode for the PostgreSQL external database
The SSL mode for connecting with the external PostgreSQL database. Supported values are:
- require
- verify-ca
- verify-full
See https://www.postgresql.org/docs/current/libpq-ssl.html for a description of each mode.
Any of the supported PostgreSQL modes requires enabling SSL.
Mandatory: Yes.
CA Certificate(s)
The CA certificate for validating the database SSL certificate. Click Select Files to import a file containing this certificate in PEM format and Base64 encoding.
As explained in Database requirements, the SSL certificate for the database host must include the IP address or FQDN of the host.
Mandatory: When the SSLMode for the PostgreSQL external database value is one of the following.
- verify-ca
- verify-full