For ACMEv2 clients to use External Account Binding, you must create one or more External Account Binding credentials.
An External Account Binding credential contains the following information:
- A friendly name that uniquely identifies the External Account Binding credential.
- The CA ID in Entrust CA Gateway of the Certificate Authority (CA) that will issue certificates to the ACMEv2 clients.
- The Profile ID in Entrust CA Gateway of the certificate profile that defines the certificate type issued to the ACMEv2 clients.
- A list of permitted algorithms that ACMEv2 clients can use for enrollment with External Account Binding.
- An HMAC (Hash-Based Message Authentication Code) key that new ACMEv2 clients will use to create an account. The key will be created when you create the External Account Binding credential.
- The Key ID of the HMAC key for the External Account Binding credential. New ACMEv2 clients will use this Key ID to create an account. The Key ID will be created when you create the External Account Binding credential.
- An ACMEv2 Request URL that ACMEv2 clients must use to access the External Account Binding credential and perform ACMEv2 operations. The URL will be created when you create the External Account Binding credential.
Multiple ACMEv2 clients can use the same External Account Binding credential to create an account and perform ACMEv2 operations.
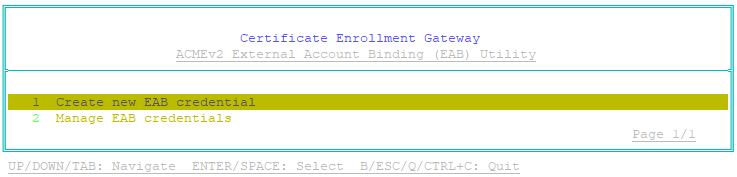
To create a new External Account Binding credential
- On the Entrust Deployment Manager or Cryptographic Security Platform node hosting the EAB Utility, log in as sysadmin.
- Enter the following command to launch the EAB Utility:
sudo eab-util - The main menu appears:
- Select Create new EAB credential, then press Enter.
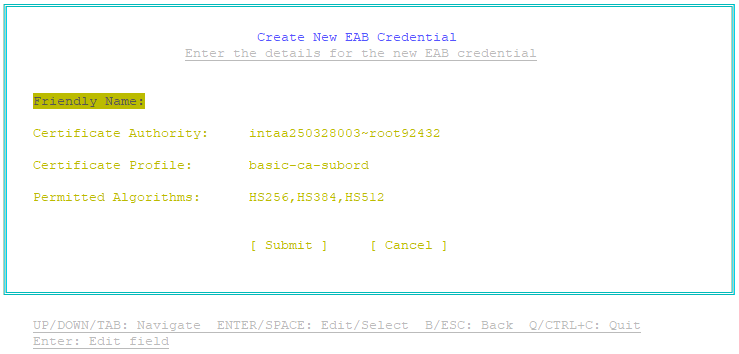
The Create New EAB Credential page appears. - Each External Account Binding credential in the EAB Utility is identified by a unique string called a friendly name. Provide a friendly name for the credential:
- Select Friendly Name. then press Enter.
- Type a friendly name for the credential. The name must start and end with an alphanumeric character. The name must be a maximum 25 characters long. The name can contain uppercase and lowercase letters, numbers, spaces, and the following non-alphanumeric characters:
, ! @ # & * : ( ) - Press Enter.
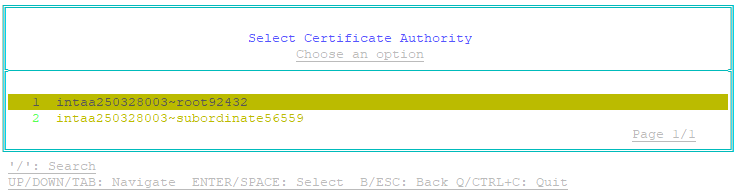
- Select the Certification Authority that will enroll the ACMEv2 client for a certificate:
- Select Certificate Authority, then press Enter.
The Select Certificate Authority page appears. - Select a Certification Authority from the list, then press Enter.
- Select Certificate Authority, then press Enter.
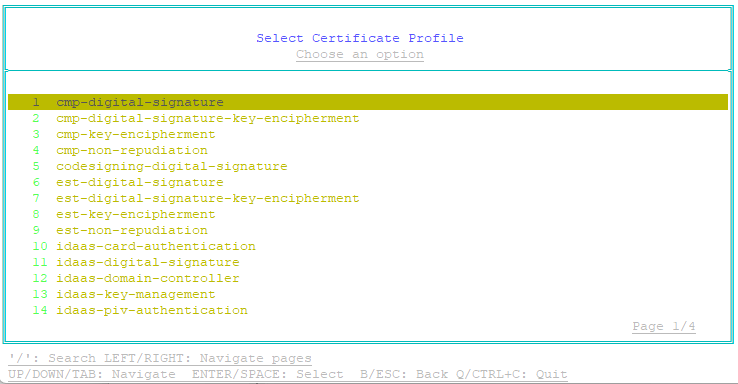
- Select the certificate profile defined in CA Gateway that will be used to issue the certificate to the ACMEv2 clients:
- Select Certificate Profile, and then press Enter.
The Select Certificate Profile page appears. - Select the certificate profile that will issue the certificate to the ACMEv2 clients, and then press Enter. For Entrust PKI as a Service, the profile ID is one of the following:
- privatessl-tls-client-server
- privatessl-tls-server
- privatessl-tls-client
- Select Certificate Profile, and then press Enter.
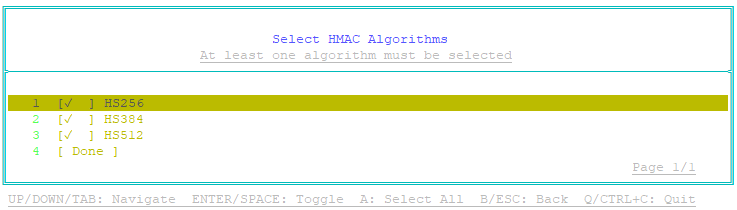
- Select the algorithms that ACMEv2 clients can use for enrollment with External Account Binding:
- Select Permitted Algorithms, and then press Enter.
The Select HMAC Algorithms page appears. - You can enable or disable an algorithm by selecting the algorithm, and then pressing Enter or spacebar. A checkmark next to the algorithm indicates that algorithm is permitted to be used for External Account Binding.
- Select Done, and then press Enter.
- Select Permitted Algorithms, and then press Enter.
- Select Submit and then press Enter.
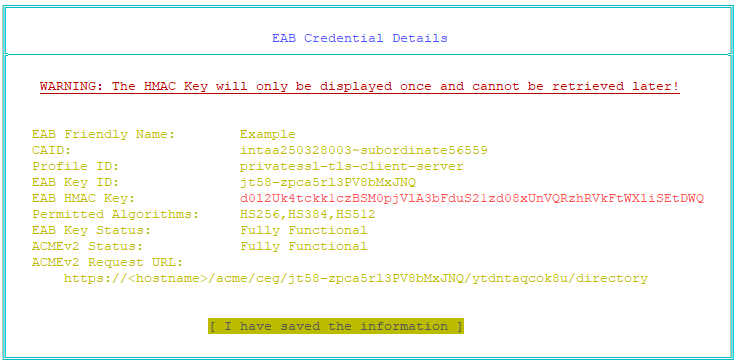
The External Account Binding credential is created. The EAB Credential Details page appears. For example:The HMAC key will be displayed only on this page, and cannot be retrieved later. You must copy this HMAC key before closing the page.
- Copy the information. The ACMEv2 Request URL and HMAC key are required to enroll the ACMEv2 client for a certificate.
- Press Enter to return to the main menu.