The Entrust WSTEP Service is a component of Certificate Enrollment Gateway. The Entrust WSTEP Service is Certificate Enrollment Gateway’s implementation of the WSTEP protocol.
The Entrust WSTEP Service will use Windows certificate templates when enrolling users, computers, or domain controllers with your Windows-native endpoints. Create as many new certificate templates as you require. For example, users may require certificates with two key pairs (such as Encryption and Verification) or one key pair (such as Signature or Encryption).
To create a Windows certificate template for WSTEP
- Log into Active Directory as a member of the Domain Admins group.
- Run
mmc.exe(Select Start > Windows System > Run, then entermmc.exe).
The Microsoft Management Console appears. - Select File > Add/Remove Snap-in.
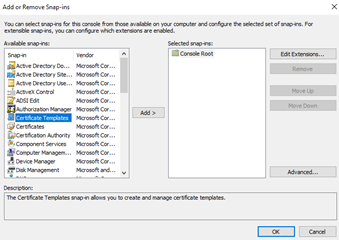
The Add or Remove Snap-ins dialog box appears. - In the Available snap-ins list, select Certificate Templates.
- Click Add.
- In the tree view, select the Certificate Templates snap-in.
- Select the certificate you want to duplicate for the enrollment service. Supported templates:
- Computer
- Domain Controller
- Kerberos Authentication
- User
- User Signature Only
- Duplicate the template by selecting Action > Duplicate Template. A Properties of New Template dialog box appears.
Under each tab, configure template options as described in the following sections.
Start configuring the template options from the Compatibility tab. Otherwise, the Provider Category option in the Cryptography tab will be locked to Legacy Cryptographic Service Provider.
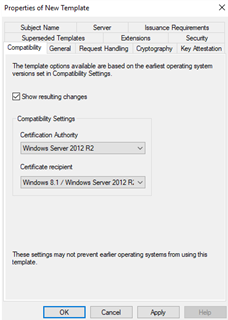
Compatibility tab
Under the Compatibility tab, select the compatibility settings based on the earliest versions of the operating systems running in your environment.
Option | Minimum version |
|---|---|
Certification Authority | Server 2012 R2 If you install a Windows Server 2016 CA, read the following Microsoft troubleshooting guide: Cannot select Windows Server 2016 CA-compatible certificate templates from Windows Server 2016 or later-based CAs or CEP servers. |
Certificate recipient | Windows 8.1 / Server 2012 R2. Earlier versions of Windows may not recognize template options introduced in later versions of the Windows certificate templates. |
General tab
Under the General tab, configure the supported options.
Option | Supported | Value |
|---|---|---|
Template display name | Yes | The display name for the new certificate template. |
Template name | Yes | The name of the new template. The default value of this field is the value set in the Template display name field but without spaces. We recommend using this value. The name must contain only alphanumeric characters (a-z, A-Z, 0-9). |
Validity Period | Yes | Any value allowed by the validity policy of the issuing CA. |
Renewal Period | Yes | Controlled by the client. |
Publish certificate in Active Directory | No |
Security tab
Under the Security tab, set the following options.
Option | Value |
|---|---|
Groups or usernames | Select the group that will use the new certificate template. For example, select the Domain Users group to use a copy of the User certificate template. If the group is not listed, click Add to add the group to the list. |
Permissions for Authenticated Users | Set the following Allow permissions for the selected group: Read, Enroll, Autoenroll. |
Request Handling tab
Under the Request Handling tab, set the supported options.
Option | Supported | Value |
|---|---|---|
Purpose | Yes | Encryption, Signature, Signature and encryption, and Signature and smartcard logon |
Delete revoked or expired certificates (do not archive) | Yes | |
Include symmetric algorithms allowed by the subject | Yes | SMIME settings |
Archive subject’s encryption private key | No | |
Authorize additional service accounts to access the private key | No | |
Allow private key to be exported | Yes | |
Renew with the same key | Yes | |
For automatic renewal of smart card certificates, use the existing key if a new key cannot be created | Yes | |
Enroll subject without requiring any user input | Yes | |
Prompt the user during enrollment | No | |
Prompt the user during enrollment and require user input when the private key is used | No |
Cryptography tab
Under the Cryptography tab, set the supported options.
Option | Supported | Value |
|---|---|---|
Provider Category | Yes | |
Algorithm name | Yes | |
Minimum key size | Yes | 2048 |
Requests can use any provider available on the subject’s computer | Yes | |
Requests must use one of the following providers | Yes | |
Request hash | Yes | |
Use alternate signature format | No |
Key Attestation tab
Options under the Key Attestation tab are not supported.
Subject Name tab
Under the Subject Name tab, set the supported options.
Option | Supported | Value |
|---|---|---|
Supply in request | Yes | The Subject Alternative Name RegisteredID is not supported. The Subject name types Title and Initials are not supported. |
Use subject information from existing certificates for autoenrollment renewal requests | Yes | |
Build from Active Directory information | Yes | |
Subject name format | Yes | For User certificate templates, the following formats are supported:
For Computer or Domain Controller certificate templates, the following formats are supported:
|
Include e-mail name in subject name | No | |
E-mail name | Yes | |
DNS name | Yes | |
User principal name (UPN) | Yes | |
Service principal name (SPN) | Yes |
Issuance Requirements tab
Options under the Issuance Requirements tab are not supported.
Option | Supported |
|---|---|
CA certificate manager approval | No. All certificate requests are processed automatically without any approval. |
Require the following for reenrollment | No |
Extensions tab
All options under the Extensions tab are supported.
See the following table for the Key Usage combinations supported by each Purpose in the Request Handling tab.
Purpose | Supported Key Usage Combinations |
|---|---|
Encryption | Key Encipherment |
Signature | Digital Signature Digital Signature+Non-repudiation |
Signature and Encryption | Digital Signature+Key Encipherment |
Signature and smartcard logon. | Digital Signature |