Preparing the service account for Kerberos
After Configuring an Active Directory in the agent, click Next to display the Preparing Service Account for Kerberos dialog.
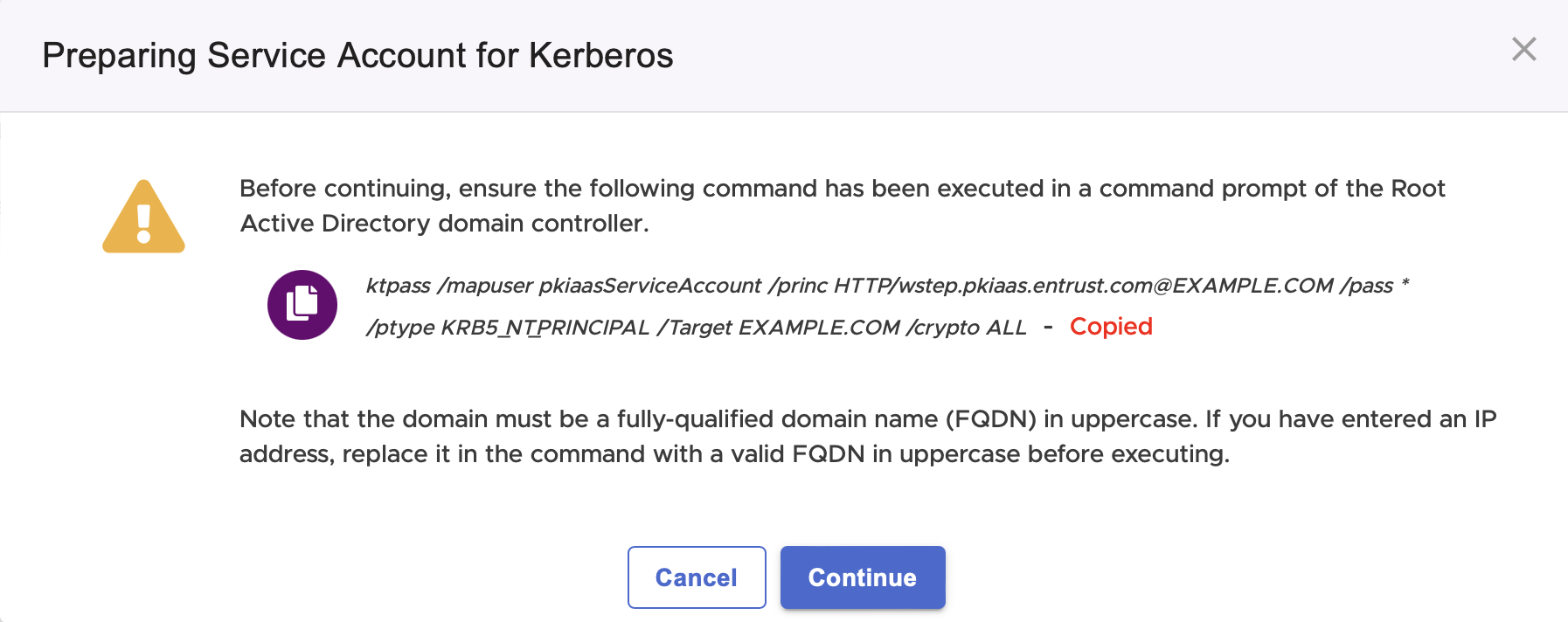
If you have not yet executed the displayed command:
Click the icon to copy the command.
Log in to the server hosting the root Active Directory domain controller as either:
A domain administrator
A user who is a member of the built-in Account Operators domain group.
Paste the command in the Windows PowerShell.
Replace the value of the /pass option with the password entered when Creating a PKIaaS WSTEP Service Account.
Run the command.
Specifically, this ktpass command maps a Kerberos Principal to:
The Service Principal Names (SPN).
The User Principal Name (UPN).
These mappings are necessary for compatibility with AES128 and AES256 algorithms in Kerberos Authentication.
See below for the command syntax.
ktpass /mapuser <USER> /princ HTTP/<PKIAAS-WSTEP-URL>@<UPPERCASE-DOMAIN-NAME> /pass <PASS> /ptype KRB5_NT_PRINCIPAL /Target <UPPERCASE-DOMAIN-NAME> /crypto ALL|
Parameter |
Value |
|
<USER> |
The name of the user described in Creating a PKIaaS WSTEP Service Account. |
|
<PKIAAS-WSTEP-URL> |
The region-specific URL for Entrust PKIaaS WSTEP. |
|
<UPPERCASE-DOMAIN-NAME> |
The domain selected when previously Configuring an Active Directory in the agent, in uppercase. |
|
<USER-PASSWORD> |
The password of the user described in Creating a PKIaaS WSTEP Service Account. |